| Week 1 |
Introduction to Documentation |
Evernote, Blogger
Set up Evernote and Blogger accounts.
Tuesday Homework:
- Find a recent article on "hacking" and write a response to it in Blogger
Wednesday Homework:
- Read 'Sure Thing' by David Ives. Write a blog about why this is being assigned. Also write about what might be problematic with the ending.
- Read Chapter 1 of This Machine Kills Secrets.
|
| Week 2 |
Introduction / Safety / Basic Electronics / Soldering / Breadboards |
Lesson:
Basic Electronics
Using a Multimeter
Electromagnetism
Activities:
- Find at least one website that explains electromagnetism and collect 3 images
- Create a DIY Pickup
- Create a Jumping Speaker
- Experiment with Headphones and Amps
- Connect a DC motor to 1/4" phone jack
- Create a Piezo Contact Mike
Homework:
- Find a recent article on "hacking" and write a response to it in Blogger
- Introduction to The Design Process:The Deep Dive. Write a blog post about how one might combine hacking with the design process.
- Listen to Word Watcher. Write a response in a blog post.
- Look up Richard Lerman's miniature instruments made with piezo disks or any other Piezo instrument. Write a description of both the instrument and how it is played.
- Look up Jérôme Noetinger, Andy Keep, Nathan Davis and describe how they have used magnetic music. Describe your own idea for an electronic instrument.
- Start CodeAcademy's Python Courseand continue until over the semester until completed
Documenting:
- Context (critical factors influencing the story such as location, project objectives, assumptions, hypothesis, timeline)
- Specific actions and activities you undertook (while also answering what assumptions led you to act in this way?)
- The result (Why did the failure or success happen? Then ask why a few more times. What happened? What does this mean for the assumptions and hypothesis raised earlier? Why was it a failure/success? What are the big picture/long- term impacts?)
- The learning (What was learned and has changed because of the failure/success)
- So What? (What results did changing create or is likely to create, implications for the future, how has the learning been institutionalized, recommendations for other projects in similar situations)
|
| Week 3 |
Tape Heads |
Tape Head Hack
Be Laurie Anderson for a day.
Acquire or remove a tape head from a casette player and connect it to a mini amp. Play back recorded material.
Homework:
- Listen to Hacker Law and write a response
- Research Nam June Paik's 1963/2000 "Random Access" magnetic tape piece. Collect at least one image. Describe the piece and the technology involved, then write your thoughts about it and recreate a smaller version. (
Or research Laurie Anderson's Tape Bow Violin (1977). Collect at least one image. Describe the piece and the technology involved, then write your thoughts about it and recreate your own version. Laurie Anderson - Home Of The Brave (1986) FULL 22:12.
- Read Chapter 1 of This Machine Kills Secrets and write about whether you believe Bradley Manning act was political.
Documentation:
Once you have successfully created your magnetic tape piece, make a short (2 min < 5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date
|
| Week 4 |
Circuit Bending |
NAND, Schmitt Triggers and 3D Printing
Design your own simple oscillator.
Introduction to 123D Design. Create a 3D model prototype.
Homework:
- Listen to Internet Crisis and write a response
- Find a recent article on "hacking" and write a response to it in Blogger
- Read Chapter 1 of Blown To Bits: Your Life, Liberty, and Happiness After the Digital Explosion by Hal Abelson Ken Ledeen Harry Lewis Pp. 1-17. This chapter makes the point that today everything is digital -- that is, everything is represented by binary digits or bits.
Answer the following questions:
- What does it mean to say that the bit is the natural unit of information? What information is represented by bits today?
- What is Moore's Law?
- Someone offers you a summer job and offers you two payment schemes:
- $10 per hour for 40 hours per week for 30 days or
- One cent on day 1, two cents and day two, four cents on day three and on (doubling each day) for 30 days.
Which play would you choose? Explain.
- Give an example of how the digital explosion is "neither good nor bad" but has both positive and negative implications.
- Describe the heart of the chapter in two words.
- Information" is not the same thing as "Data". What if I gave you an 8" floppy filled with data?.
- SSNs are issued following a structure based upon the state and time of issue. In particular, the first 3 digits are assigned to particular states, and digits 4-5 are issued based on the time of issue.
- What are the advantages of such an approach? Law enforcement claims that the structure helps to fight fraud. How so?
- How might this structure be exploited to commit identity theft? Think of a plausible, real-world example.
- If SSNs could be randomly assigned, who would it help, and who would not be helped?
Documentation:
Once you have successfully created your hack, make a short (2 min < 5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date
|
| Week 5 |
Circuit Bending/Blinky Lights |
A Hex Inverter Audio Oscillator
Design your own audio oscillator. Create a 3D model prototype.
Homework:
- Listen to Emmanuel Goldstein
and write a response
- Find a recent article on "hacking" and write a response to it in Blogger
- Read Chapter 2 of Blown To Bits: Your Life, Liberty, and Happiness After the Digital Explosion
by Hal Abelson Ken Ledeen Harry Lewis. This chapter describes the various ways in which or personal privacy is compromised by the digital explosion.
- Complete the following activity: Metadata in a word document
- Take an inventory of your digital footprints and fingerprints.
Digital footprint:
- Email accounts
- Online banking services
- Social networking applications
- Web-based applications (e.g., Google Docs, Flickr)
Digital fingerprints:
- Web browsers (cookies, Google Web histories, Amazon browsing history)
- Navigations systems
- Cellular phones
- EZPass
- Loyalty cards
- Metrocard
Once you have determined your digital footprints and fingerprints, choose the best explanation for why you have forgone privacy and revealed personal information.
For digital fingerprints, you may not have made a conscious decision to trade-off privacy for any reason. However, now that you are aware of the tradeoffs, list the reason that best fits, or indicate that you plan to change your behavior in the future.
Visit this website:
www.komar.org/cgi-bin/ip_to_country.pl
Explain how the site can determine:
- where you are located.
- what web browser you are using.
- what operating system you are running.
- Answer the following questions:
- What is an RFID tag? What does it do? How could you use RFID tags? How could institutions use RFID tags? How could government use RFID tags?
- What is EDR? What does it do?
- What's the difference between "big brotherism" and "little brotherism"? Do you think having security cameras everywhere is good or bad?
- Is the Privacy Act effective? Explain.
- Is it possible to identify a person, knowing just his or her gender, birthdate, and zip code? Explain.
- Do you think that the convience of technology outweighs the privacy concerns the technology causes? Would you be willing to give up these things in order to have more privacy?
Documentation:
Once you have successfully created your hack (whether just the breadboarded circuit or a prototype), make a short (2 min < 5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date
|
| Weeks 6-7 |
More Circuit Bending |
A Preamp and a CMOS Hex Inverter and more 3D Printing
Design your own sound generator.
Build all the circuits and choose one to create a prototype. Feel free to experiment with components to construct your own circuit.
Homework:
- Read Hire The Hackers,
Hardware Hacking and Inside the Lair of the Hardware Hacker
and write a response
- Find a recent article on "hacking" and write a response to it in Blogger.
- Watch http://www.stealthisfilm.com/Part1/ and write a response
From their origins in the trash room of a non-profit in Manhattan to their emergence as the instigators of an international art movement, Graffiti Research Lab: The Complete First Season documents the adventures of an architect and an engineer who quit their day jobs to develop high-tech tools for the art underground. The film follows the GRL and their network of graffiti artist collaborators (and commercial imitators) across four continents as they write on skyscrapers with lasers, mock advertisers with homemade tools, get in trouble with The Department of Homeland Security and make activism fun again. Primarily using video footage from point-and-shoot digital cameras (“The Pocket School”) and found-content on the web, the movie’s visual style draws as much from the art of the power point presentation and viral media as conventional documentary cinema. Narrated by GRL co-founders, Roth and Powderly, The Complete First Season makes a humorous and insightful argument for free speech in public, open source in pop culture, the hacker spirit in graffiti and not asking for permission in general. The film was premiered at the Sundance Film Festival in 2008. Available 24/7 on The Pirate Bay.GRL
- Read chapter 3 Blown To Bits: Your Life, Liberty, and Happiness After the Digital Explosion by Hal Abelson Ken Ledeen Harry Lewis and based on Chapter 2 and 3 answer 10 of the following questions:
- With the amount of information available about people's personal lives so readily accesssible, identifiable by process of elimination even after it has been de-indentified, should there be stricter regulations about who can access such information, and how much information should even be available to the general public?
- Is it better to be too private or too public? Does it make a difference if we're talking about people or companies?
- Do you think benefits of digitizing our world is worth the sacrifices? What are the sacrifices?
- "Millions of Americans are victimized by identity theft every year, at a total cost in the tens of billions of dollars annually." In your opinion, is this loss of privacy worth the convenience of technology?
- How are physical data on paper and bit data interacting?
- Considering that postings on social networks like www.dontdatehimgirl.com, www.platewire.com and www.rottenneighbor.com cannot be checked for authenticity, should they be legal? What, if any, security threats do them pose?
- How can we regulate privacy in the digital age?
- If RFIDs are embedded into all newly printed currency in the U.S., what would that mean for the society as a whole?
- What is the risk of using services like Google Docs and cloud computing?
- The amount of bits that exist already and are being created every year is enormous and growing at an exponential rate. This has a lot of benefits for society, but there are also some potential issues or problems. What are these problems?
- If information on computers is so easy to forge (someone could alter the name of the person who created the document or alter the time recorded of the creation of the document), how can it be trusted?
- Is it possible in society today to be completely anonymous and untraceable?
- What are your thoughts about people bashing others on social networks such as facebook? This includes posting pictures.
- In an age when everything from privacy and personal identification to security and surveillance is becoming digitized, what are some aspects of a society and characteristics of individuals that absolutely cannot be 'digitized'?
- Has technology lowered our standards for what democracy is?
- With all of our daily activities - shopping and surfing habits, for example - tracked, how can we keep our own "private" hobbies and interests without constantly feeling exposed?
- The advance in technology has created new "cultures", such as the email culture, web culture and credit card culture. Do these "new cultures" actually bring us significant benefits?
- How to we deal with the problem of technology constantly becoming obsolete, resulting in losses of information stored in out-dated devices?
- Technology is continually advancing, changing the way our world runs. With these advancements, technology seems to take over jobs once held by actual people (fast-lane RFID systems taking over the work of highway toll collectors). Do these advancements benefits outweigh their damages on the overall economy?
- How much privacy should we surrender (legally and otherwise) to ensure safety?
- We are in the center of a rapidly expanding world of communication and access to information through the internet. However, many other countries, particuarily in Africa, still face multiple constraints (inconsistent electricity, faulty local telephone networks, affordability of equipment, etc) in providing internet access to all. What steps must be implemented in order to contribute to the development of Internet access in developing countries?
- The reading talks about a lot of footprints and fingerprints that we leave behind. Most of their examples have been about the negative impacts about technology, and how it has changed communication in our society today. Are there positive aspects?
- Has the proliferation of technology taken the place of real relationships between people?
- Do you think it would be possible or even helpful to create a new set of laws restricting access to certain records or requiring investigators or government officials to ask permission to look through data like that recorded in a car's event data recorder (EDR)? An EDR records all of a cars moves, I.e turn signals, brakes, speed, seat belts, etc.
- Are any of the privacy issues scary enough to shift your daily habits?
- List the five footprints/fingerprints mentioned in the reading that are most interesting to you, briefly explaining what they are and why you find them interesting.
- Identify situations where rapid growth in computing power, storage capacity, or communication speed has rendered a particular product or business model obsolete and created new opportunities.
- How do you feel about keeping your personal information on a computer? How could you keep your information safe in a practical way?
Documentation:
Once you have successfully created your hack, make a short (2 min < 5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date
|
| Week 8 |
Programming |
Homework:
- Problem Solving Basics and Computer Programming
- Complete SNAP programs at home
- Read Chapter 4 of Blown to Bits and
answer the following questions:
- "The architecture of human knowledge has changed as a result of search." What does this claim mean? Do you agree?
- When you type a word or phrase into the Google search engine, does it search the web? Explain.
- Think of a number between 1 and 100. If you tell me "too high" or "too low" I can guess the number in 7 guesses. How come?
- p. 144: "Google emerged -- from this dilemma at least -- with its pocketbooks overflowing and its principles intact." Do you agree?
- Using three search engines:
- www.google.com
- www.yahoo.com
- www.bing.com
Do several searches and compare the results. There are a number of tools available on the web that will help, but you can get a very good idea of the differences simply by looking at what you see on the first page or two. Since users rarely get past the first page, being there matters.
Much of the power of search technology to influence users comes from presenting results in an ordered list. Users generally believe that the top links are “better.” There are, however, alternatives to presenting results in a simple list.
Take a look at several of the alternatives and share your thoughts and observations. Some examples:
- www.kartoo.com
- www.searchme.com
- www.quintura.com
Google tracks everything that everyone queries. Privacy issues aside, the results are fascinating. You can find them at www.google.com/trends. Pick a topic and look at the results. What conclusions do you draw? Include the topic and date and time that you searched.
|
| Week 9 |
SNAP/BYOB |
Makey Makey
Assignment: Make a scratch project connected to the Makey Makey
Homework:
- Find a recent article on "hacking" and write a response to it in Blogger
- Read Senate Advocates and The Jargon File and write a response.
- Read Chapter 5 of Blown to Bits.
Use Vigenère cipher
vigenere cracking tool or sharkysoft.com:
- Using the key “HarryLewis” create a Vigenère cipher and encrypt the message: “BlowntoBitsRocks.”
- Use the same key to decode
Nofxjp xniurs vmcccppaug kyye irmjfoev ofinqwz. Piztlgu qkzuvj ydmzm, loe ivqfppa sye wrqnmjilpnx. Pmf gwv xpnu kfpq wb odw.xfmrpa.kgt/tivlow. Lqur a kfntg wvv sofb ye xdm jlslcrd. Adil joetjfwewfz df pmf hnio? Pntcsoi ppw aogza lrz lsae reb emim loak pmf waijjhvu.
-
The following cipher text was encrypted using a Vigenère cipher. Decipher it and write down exactly where it can be found:
GWKLI CICBV WKPTM OBZLH FCDVF PTNFP SOOAT QJBUD IIMLI SKYST WATQV KOOBF HOBNX QEDOS JOSJX LISGK NMTYB WBIFB MGEOM SUQLL SISSO IJMJH SZSMV ATSGO OAXLI SKYST WATQV KOOBF HPSMB CLWPT OXFVZ AOSSB JVZVF JSVPX FWOHH RBBAS TVOZQ MGWER IBJVZ LISZK TBWWD OROJB BKOCK ZPALA CZSSO XKAOQ WZMMM GSSAO NJXJF JSBZB AAOUH RBBTF ZCBOT IRKXF WDFAL AOUGN SIPKP FDRPB HYSOD RTMOW SMHRJ VZAGR WQJBB RFRHR FEHJM RVKTM GGVUV NJADK BBRWF UHJZQ VSQAM GTOJO JBTDM TCBBA EGOUO CDQOA MWNKU QHFDO BUFMI HSCRE DQGYD CAZVB XJTOB NEQLC EFWFF ATFEU ZYCIE UPADE UMKFF HKYSS LUBBA KLMBL BJOSM IUDFH COWMK QXVSB FQGLI SKYST WSMAC CUQGK UOBDM GBFDS BDVZB WTUCX FJRGU VSBTU TQIOJ OEZXS NSRDI MLWUV WXHAV GVZRR BXIWO WBEUW IABBT KOBTK JSGYS QGFJU VDNIK WTPID OWPAU QOXII IHFBO XEQLT FUWXO QGYUC VKQXX FSWUR UVHOH CJOSV FWOHG KOLMZ FCHRF ZBFTH WDVBB GOGCP ICFSO GCMJM MAFGO BFLXU JRWXH EASUI GOUWF SLSCP UPBKQ CHOOB BSMSJ OSGHF FBSOE AMGLB CGXPT LJGQR BVZAO UWXUP XOPFZ NBATJ FGIVU WYLIW GOYXE GTWCX PNWAH WHKMQ GXPFA KUQHF FJSBZ WGWTV CEMLD FPKKR BBWWD WGSPV LSSSP OJVZE BRSDI IMOJZ ZKGNX UUHVO JZEAW SGDIM EAWSG YGBAW JFQRJ TWJFB OXEOK SORQR JTWJF BOXEM OWSMC XFEAG DCAOT IYLFF
The ciphertext above is quite long making it easier to break. Why is that so? What would happen if the text were exactly the same length as the key?
- Essential Security (www.essentialsecurity.com), a new startup, offering free, easy to use software to encrypt email.
- They raised venture capital saying that they used off-the-shelf encryption software. Would they have been better saying that they had a secret, proprietary encryption algorithm?
- Given how easy it is to use, why don’t you and your friends encrypt email messages?
- Complete the following exercise: Suppose g=43, p = 19 . If your “secret code” is 17, using the Diffie-Hellman key exchange protocol,
- What is your “Public” key?
- Amazon’s Public key is 6. What is your “shared key”?
Documentation:
Once you have successfully created your hack, make a short (2 min < 5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and send the link before class time on the due date
Reading:
Resources:
|
| Weeks 10-12 |
Microcontrollers |
Lessons:
- Arduino Intro
- Taking Projects: Home EMSL boards
- Arrays
- Random Numbers
- Interrupts
- Arduino Data Storage
- Working with XBees
Activities:
- With your team, design an object with a button, buzzer and at least one LED
With your team design an object with a tilt sensor.
- With your team create a plush toys with wireless communication.
- Option 1: Find an interesting sensor and implement it such that you can get data from it into a computer. You may use the Arduino interfaces, or another if you like. Make sure to research your sensor first to know if any support circuitry must be built around it to make it functional and to protect the interface.
Option 2: Build a sensor from scratch. You may recreate any of the sensors described in the Forrest Mims book or create another. The sensor should produce some variation measurable by a multimeter (i.e. voltage, resistance, etc.).
Homework:
- Find a recent article on "hacking" and write a response to it in Blogger
- Read The Lost Art of Phone Phreaking, Secrets of the Little Blue Box and Wargames
and write a response.
- Read Chapter 6 of Blown to Bits
Write about some aspect of society, industry, the arts, education, etc., that is being transformed by the information revolution. Your topic should be on something that is being done differently today than it was five years ago or that will be different five years from now. Keep the ideas small, don't write about college admissions, but maybe “How the availability of statistical data on high school sports players might affect college recruitment”
- How are people using information and communication now?
- How did they used to do it, before there were computers and databases and rapid
communication of digital data?
- How will this part of the world have changed in five years if the trends continue as they
have?
- How should things be in the future?
- Is it wrong to illegally download music using P2P software such as BitTorrent and Kazaa? Why or why not?
-
The RIAA goes after illegal downloaders (sometimes falsely). Is this a deterrent? Should they do this to protect their artists?
- The claim is that it costs $750 per song infringed in an illegal downloading case. Why is it so high? Is this a fair and reasonable amount?
-
Is it right that a person should have secondary liability when their computer or internet connection is party to illegal file sharing without their knowledge?
- Many media files now come with Digital Rights Management (DRM) restrictions placed upon them. How do you feel about DRM? Should it be used? Is it a necessary evil?
- Does the 1998 Digital Millenium Copyright Act (DMCA) law encourage or limit innovation? What is its impact on file sharing and piracy?
- Read Chapter 7 of Blown to Bits and Chapter 8 Blown to Bits
- As a teenager, do you face monitoring or censorship by your parents? Do they let you watch R-rated movies? Listen to music with explicit lyrics? Do they let you have a cell phone? A car? Do you have your own computer, or use a shared family computer? Do they monitor your internet usage, and/or run a site blocker to stop you or siblings from viewing inappropriate materials online?
- Should sites like MySpace, Facebook, etc. be totally uncensored, or should they allow any content whatsoever to be posted and transmitted? What content (if any) should be forbidden? (hate speech, defamation, profanity, pornography, child pornography, drug trafficking?)
- What, if anything, should sites like MySpace, Facebook, Twitter, etc. do about the problem of sexual predators and other crime that may be facilitated by their services? Are they at all liable for such events if they occur? (Are they more like a distributor/truck, a newspaper/publisher, or a library?)
What is the difference between the online filtration policies employed by CompuServe (uncensored, legally safe) and Prodigy (censored, possibly legally liable).
-
Have you ever used a pre-WWW communication site such as a BBS, gopher, IRC, etc.?
Documentation:
Once you have successfully implemented your sensor, make a short (5min) video documenting your tools, techniques, and outcomes. On a Mac, you may wish to use the application iShowU to collate video of your demonstration with video screen shots of the resultant data, etc. Upload your video to google video, youtube, or other online resource and send the link before class time on the due date.
References
Mims, Forrest. Electronic Sensor Circuits & Projects.
|
| Week 11 |
Actuator Instrument |
Assignment
Using an interface construct an instrument that acts on the physical world based on computer generated commands. Actuators include motors, stepper motors, solenoids, electromagnets, muscle wire, etc. You may, but need not, incorporate sensors to control the function of the actuators.
Documentation
Once you have successfully created your actuator instrument, make a short (5min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date.
|
| Week 12 |
Sensor Instrument |
Arduino, MIDI and GarageBand
Using some form of sensing technology build a versatile sensor instrument. This instrument should include at least one sensing mechanism, a hardware interface to the computer, and software mapping/processing of the sensor data.
Aim for interesting relationships between sensed states and resultant outcomes. Be subtle. Make sure that there is a way to control the outcome. Your instrument can be easy to learn, but difficult to master.
Documentation
Once you have successfully created your sensor instrument, make a short (5 min) video documenting your tools, techniques, and outcomes. Upload your video to google video, youtube, or other online resource (TBD) and link to it in your digital portfolio before class time on the due date.
Inspiration:
BeetBox
Knock Knock – Knock interface calculator
|
| 1 week |
Microbes and electricity |
MUDWATT™ MFC KIT
This device generates low levels of electricity from microbes interacting with soil.
Explore the power of microbes with the MudWatt™ Microbial Fuel Cell (MFC) Kit. Fill the kit with soil, along with anything you find in your refrigerator. Within days the attached LED light will start to blink using only the power produced by the electricity-generating microbes in your soil!
|
| 1 week |
Microbes and electricity |
The EMG SpikerBox kit
Learn about muscle physiology through electromyograms (EMGs). You will have an understanding of neuron/muscle communication, and you will listen to the electrical impulses of muscles at rest and during contraction.
- Build the kit
- Place surface electrodes on two sides of your bicep.
- Hook up the EMG SpikerBox leads (the red and black alligator clips) to the two surface electrodes on your bicep.
- Place the reference electrode (White) anywhere on the body. In the figure above we show it attached to a metal bracelet near the wrist. You can also use another EMG electrode placed anywhere on your body, or if you have any metal rings on your fingers, you can clip the reference electrode to your ring.You can also simply hold the reference electrode in your hand.
- Turn on the EMG SpikerBox and listen for changes in activity. Do you notice a difference when you flex your muscles?
- Plug in your SmartPhone (with our free Android or iPhone apps installed) or computer (using our Backyard Brains PC app or Audacity program). Pick up something heavy. Do you see and hear a difference? The "Whoosh" is the sound of many action potentials occurring in your muscles as the muscles contract. You are listening to the conversation between your brain and muscle!
Cockroach Cyborg
|
| 1 class |
Glass recycling |
Glass is an easily recyclable material that must be separated and sorted by color for the best quality of final products. In today’s recycling industry, waste materials are separated by hand by workers on a conveyor line. This process could be automated through the use of infrared sensors.
Create a circuit that uses an infrared sensor to differentiate the colors of different glass. The outputted values are read through a serial port and can be tagged by color, allowing an apparatus to automatically determine the color of a material.
|
| 1 week |
DIY sensing |
Spectrometer
A spectrometer is a device that breaks light into a spectrum. Every element has an associated spectra. This means that recording of the spectra of different elements can provide a reliable means of identifying elements. If a certain spectrum is similar to the spectrum of a known element, you can reasonably associate that observed element with the known element.
A spectrometer is a simple device. It collects light from an object and directs that light onto a diffraction grating or spectrum, which leads light onto mirrors, which directs the light to a charged coupled device (CCD) chip, or a flat surface, which allows the spectrum to be read.
The light coming from the object is filtered into a small sliver by a collector. The thin sliver of light hits a prism or defraction grating, which splits the light into spectral lines of color, which represents the object's spectrum.The spectrum is reflected off mirrors until it reaches the chip or flat surface. Spectral lines can be identified by wavelength.
Refraction vs Diffraction
Refraction is important to the concept of spectrum because the angle of bending is dependent on the color (frequency or wavelength). Since white light (like light from the sun) contains a wide spectrum of colors, you can see light shining through a prism or sun-catcher "split" into a rainbow of colors. The shorter wavelength light (blue, violet and ultraviolet) refracts more than longer wavelength light (yellow, red and infrared) when transitioning from low density (air) to high density (glass).
A very thin, flat sheet of material constructed with a set of reflective lines and transparent spaces is called a diffraction grating or phase grating. The result of a ray of white light striking a diffraction grating is similar to the effect of a prism in that they both produce a rainbow spectrum. However, diffraction gratings have the advantage of being physically thin and often inexpensive. In fact, the PublicLab spectrometers use an inner layer of a common DVD disk as a diffraction grating because of the narrow spacing of the DVD "lines" which are imprinted there; designed to store digital data.

Diffraction produces a symmetrical pair of spectra plus the original non-diffracted light in the same direction at the source (0-deg). The prism refraction angle is higher for UV light while the diffraction angle is lower for UV light.
Light waves add and cancel from the effect of the lines and spaces of a diffraction grating. The angle of diffraction where the waves add is in direct proportion to the wavelength of the light passing through the spaces.
Parts:
- fluorescent light bulb
- spectrometer
- white paper
- calibrating
-
Spectrometer
-
Capturing Data
|
| 1 week |
DIY sensing |
Infrared Photography
monitor their environment through verifiable, quantifiable, citizen-generated data.
Infrared imagery has a long history of use by organizations like NASA to assess the health and productivity of vegetation via sophisticated satellite imaging systems like Landsat. It has also been applied on-the-ground in recent years by large farming operations. By mounting an infrared imaging system on a plane, helicopter, or tractor, or carrying around a handheld device, farmers can collect information about the health of crops, allowing them to make better decisions about how much fertilizer to add, and where. But satellites, planes, and helicopters are very expensive platforms; and even the tractor-based and handheld devices for generating such imagery typically cost thousands of dollars. Further, the analysis software that accompanies many of these devices is “closed source”; the precise algorithms used — which researchers would often like to tweak, and improve upon — are often not disclosed.
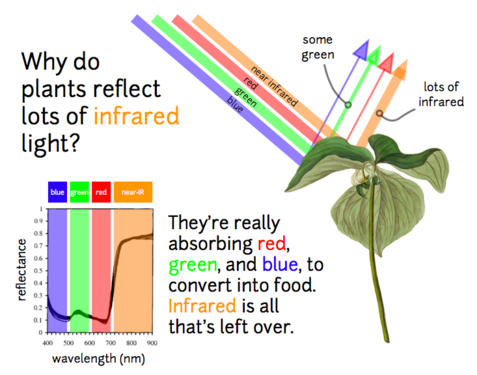
|
| 1 week |
3D model from your genome |
3dna is a Python script which derives a 3d model suitable for printing from raw genome data avaliable from services such as 23andme.
www.gullicksonlaboratories.com
Generate a printable 3D model from your genome
- A chromosome file (3dna was designed using files from 23andme, but other sources might be simular?)
- Python
- OpenSCAD
- A 3D printer
|
|
IKEA hacking |
www.ikeahackers.net
/www.apartmenttherapy.com
people.ischool.berkeley.edu
|
| 1 week |
IFTTT |
|
| 2 weeks |
Electric Imp |
|
| 4-5 weeks |
Raspberry Pis |
- Setting up our Pi
- Python:Python is cleanly designed, well documented, and relatively easy for beginners. It is also powerful and flexible and well suited for large projects.
Other important languages include Perl and LISP. Perl is worth learning for practical reasons; it's very widely used for active web pages and system administration, so that even if you never write Perl you should learn to read it.
Learning LISP will make you a better programmer.
|
|
Atoms |
IBM Atomic Shorts: How to move an atom
|


